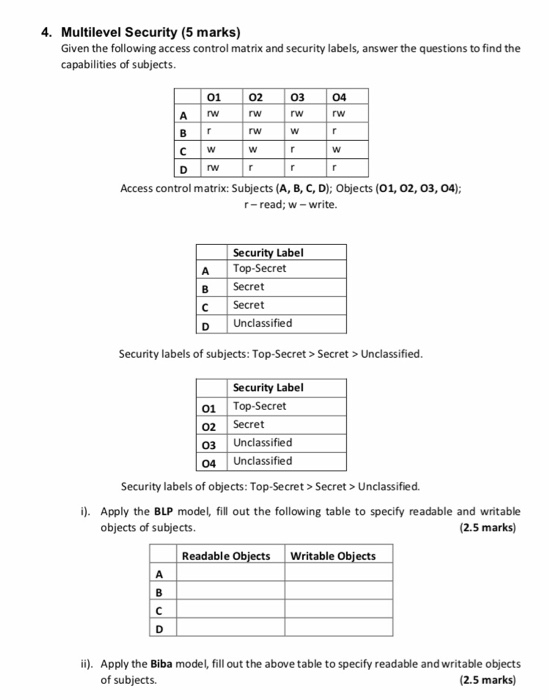
41 security labels access control
Access Control using Security Labels & Security Clearance - Isode Security policy is a generic term, but in the context of access control using security labels and security clearances it primarily relates to two things: The Security Policy defines the security label values that are valid. The Security Policy defines how security labels are matched against security clearance. The term "Security Policy" will be ... Label-based access control (LBAC) overview - IBM A security label component is a database object that is part of label-based access control (LBAC). You use security label components to model your organization's security structure. LBAC security labels In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels ...
Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to. approve read, change, and other operations

Security labels access control
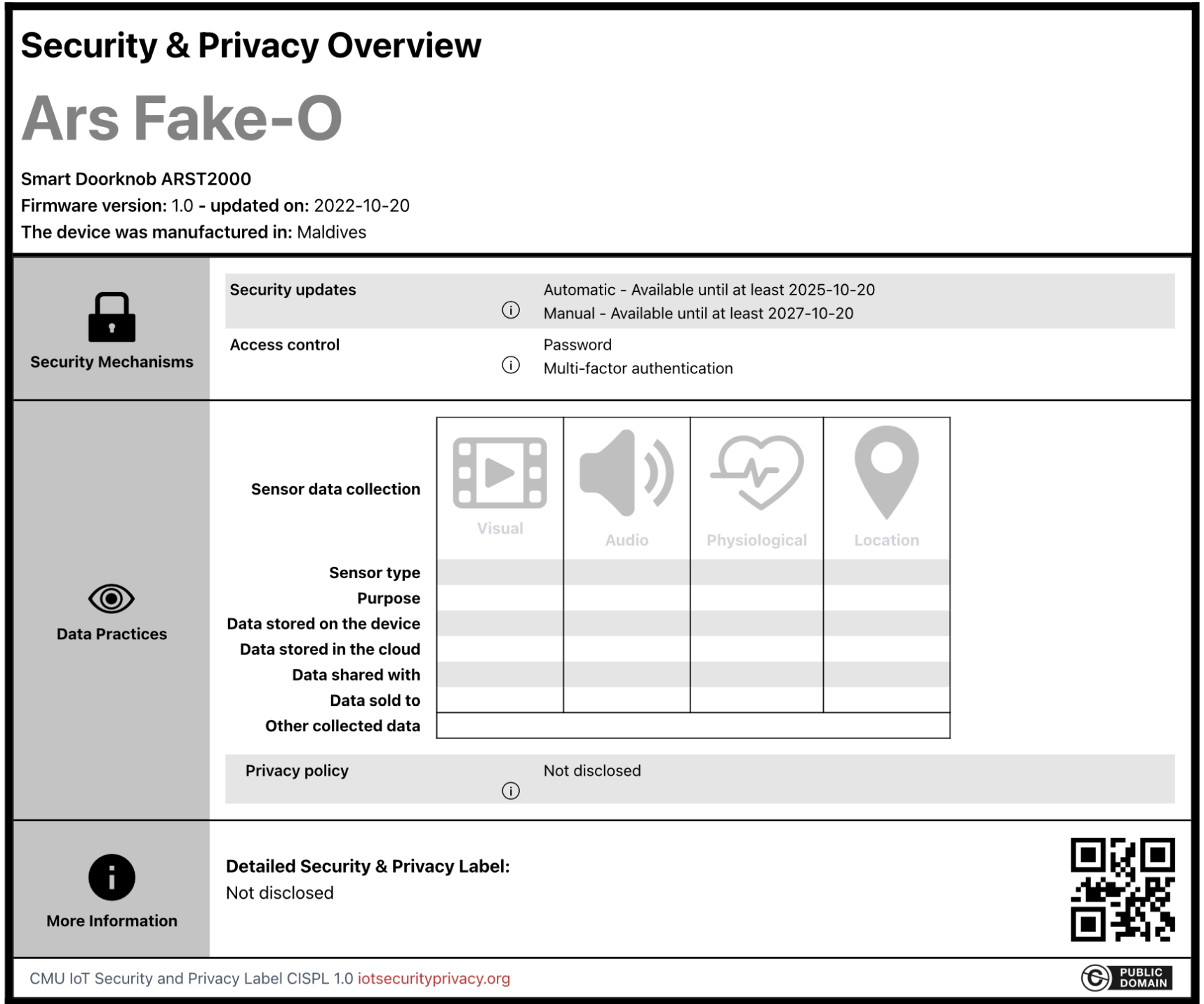
The Role of Access Control in Information Security Nov 12, 2020 · The next type of access model is known as attribute-based access control (ABAC). According to NIST: “It represents a point on the spectrum of logical access control from simple access control lists to more capable role-based access, and finally to a highly flexible method for providing access based on the evaluation of attributes.” Rare Hotel Luggage Label Grand Hotel Leoben, Styria - Austria Fantastic luggage label in excellent condition. All my labels are originals. Fantastic luggage label in excellent condition. All my labels are originals. Skip to main content. Shop by category. Shop by category. Enter your search keyword Advanced: Daily Deals; Brand Outlet; Help & Contact; Sell; Watchlist ... How security labels control access - help.hcltechsw.com Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). You construct these labels with security label components, which represent different levels of data classification and access authority.
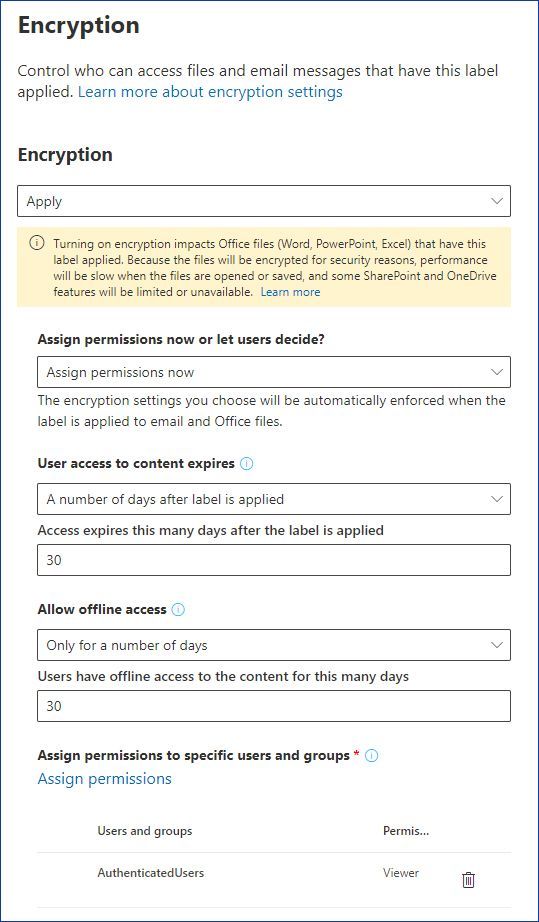
Security labels access control. Use of Security labels & access controls for nationally ... - PTC Theoretically you could 'bodge' it using separate security labels marking 'Canada only', 'UK Only' or 'Netherlands Only' and have each replica server's site principal have access to their local 'XXX Only' security label content, and not the other countries'. This means e.g a UK replica server would not be able to duplicate/host 'Canada Only' or ... How security labels control access - ibm.com Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). You construct these labels with security label components, which represent different levels of data classification and access authority. How security labels control access Home; Security You can secure your HCL OneDB™ database server and the data that is stored in your HCL OneDB™ databases. You can encrypt data, secure connections, control user privileges and access, and audit data security. Security in HCL OneDB™ The HCL OneDB™ Security Guide documents methods for keeping your data secure by preventing unauthorized viewing and altering of data or ... Using Security Labels for Directory Access and Replication Control - Isode By associating a set of Security Labels with a directory server, access controls can be applied to users accessing the directory server, by matching the user's Security Clearance with the directory servers Security Labels and requiring that at least one match be made. This allows configuration to ensure that only user with requisite Security ...
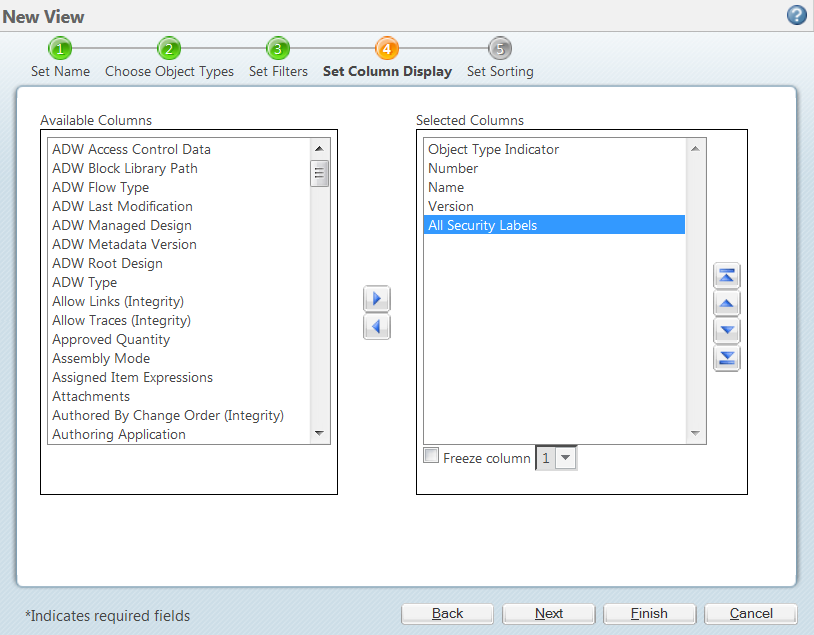
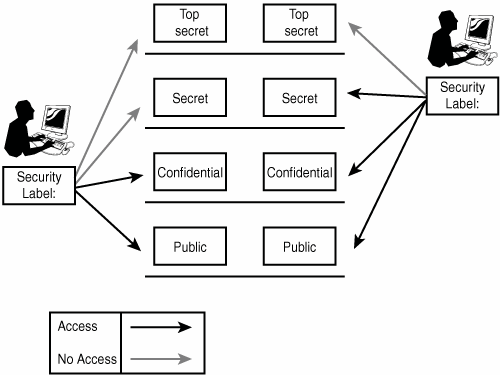
IT Cyber Security Engineer - Identity and Access Management (m/f/d) IT Cyber Security Engineer - Identity and Access Management (m/f/d) AT&S Leoben, Styria, Austria. Apply on company website IT Cyber Security Engineer - Identity and Access Management (m/f/d) Sign in to your account - admin.microsoft.com Email, phone, or Skype. No account? Create one! Can’t access your account? Access Control Models: MAC, DAC, RBAC, & PAM Explained A user may only access a resource if their security label matches the resource's security label. ... Discretionary access control decentralizes security decisions to resource owners. The owner could be a document's creator or a department's system administrator. DAC systems use access control lists (ACLs) to determine who can access that ... Label-Based Access Control The database security administrator role (DBSECADM) is required to create and maintain label-based access control security objects. Security label components Security label components are security objects for defining security policies. The elements of these components are used to define security labels, which control access to protected tables.
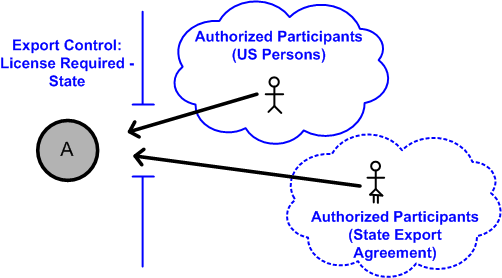
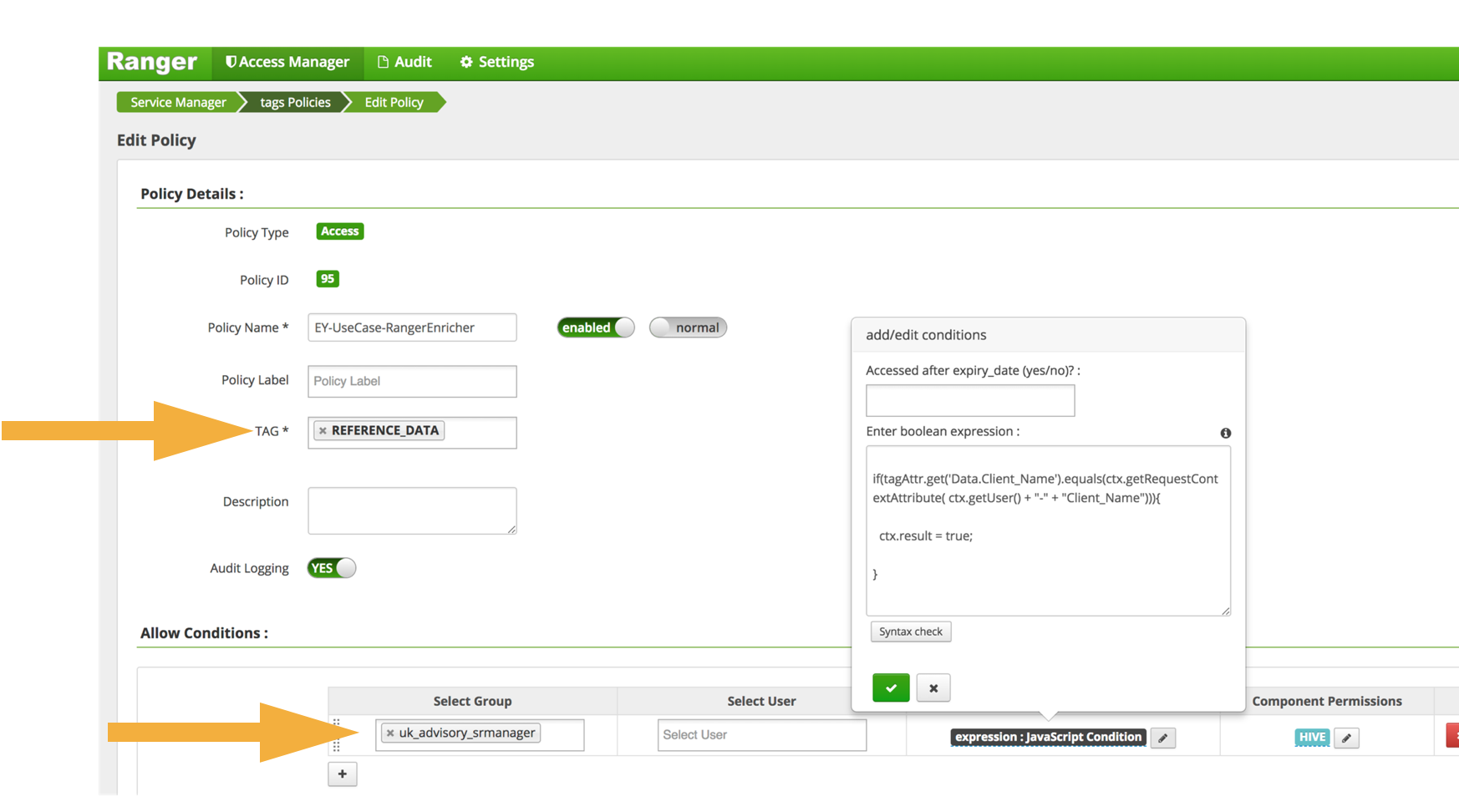
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label How to set up security labels? How to troubleshoot access control issues? Log in eSupport Login: Close: Username (Email Address) Password; Invalid username or password Cancel: Forgot password? Create a new account: Support ... Windchill PLM Permissions/Access Control/Security Label Modified: 17-Oct-2022 Applies To Windchill PDMLink 10.0 to 12.0 ... Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object. U.S. Access Board - Revised 508 Standards and 255 Guidelines The U.S. Access Board is a federal agency that promotes equality for people with disabilities through leadership in accessible design and the development of accessibility guidelines and standards for the built environment, transportation, communication, medical diagnostic equipment, and information technology. Access Control for Property Graph Data (Graph-Level and OLS) However, for applications with stringent security requirements, you can enforce a fine-grained access control mechanism by using the Oracle Label Security option of Oracle Database. With OLS, for each query, access to specific elements (vertices or edges) is granted by comparing their labels with the user's labels. (For information about using ...
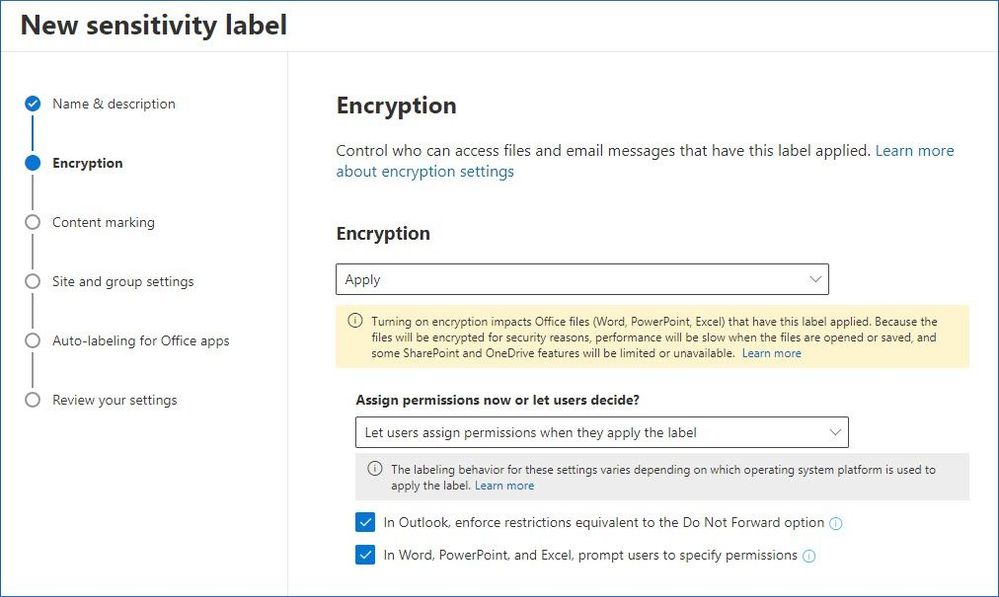
Label Security | Oracle Oracle Label Security. Control what data users see based on data and session labels. Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance.
Rare Hotel Luggage Label Grand Hotel Leoben, Styria - Austria Fantastic luggage label in excellent condition. All my labels are originals. Fantastic luggage label in excellent condition. All my labels are originals. Skip to main content. Shop by category. Shop by category. Enter your search keyword Advanced: Daily Deals; Brand Outlet; Help & Contact; Sell; Watchlist ...
Access control for projects with IAM | Resource Manager ... Oct 12, 2022 · IAM lets you adopt the security principle of least privilege, so you grant only the necessary access to your resources. IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies, which grant specific roles that contain certain permissions.
Privacy - Control - Apple Apple gives you control over the collection and use of this location data on all your devices. Starting with iOS 14, iPadOS 14, and watchOS 7, you can choose whether apps have access to your approximate location — an area of about 10 square miles — rather than your precise location. Location Services is not on by default.
Access control - Wikipedia The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap ...
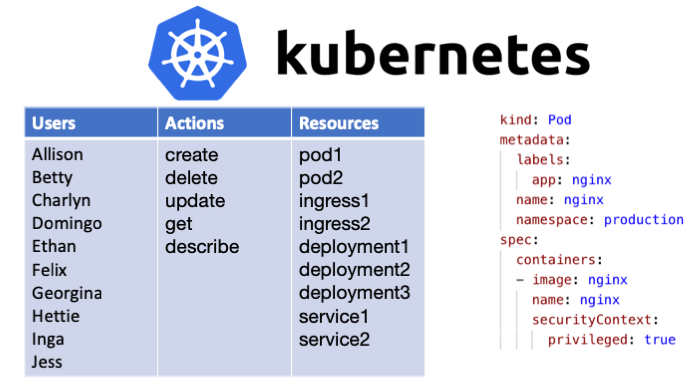
Configure a Security Context for a Pod or Container | Kubernetes Sep 30, 2022 · A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels. Running as privileged or unprivileged. Linux ...
How security labels control access - help.hcltechsw.com Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). You construct these labels with security label components, which represent different levels of data classification and access authority.
Rare Hotel Luggage Label Grand Hotel Leoben, Styria - Austria Fantastic luggage label in excellent condition. All my labels are originals. Fantastic luggage label in excellent condition. All my labels are originals. Skip to main content. Shop by category. Shop by category. Enter your search keyword Advanced: Daily Deals; Brand Outlet; Help & Contact; Sell; Watchlist ...
The Role of Access Control in Information Security Nov 12, 2020 · The next type of access model is known as attribute-based access control (ABAC). According to NIST: “It represents a point on the spectrum of logical access control from simple access control lists to more capable role-based access, and finally to a highly flexible method for providing access based on the evaluation of attributes.”
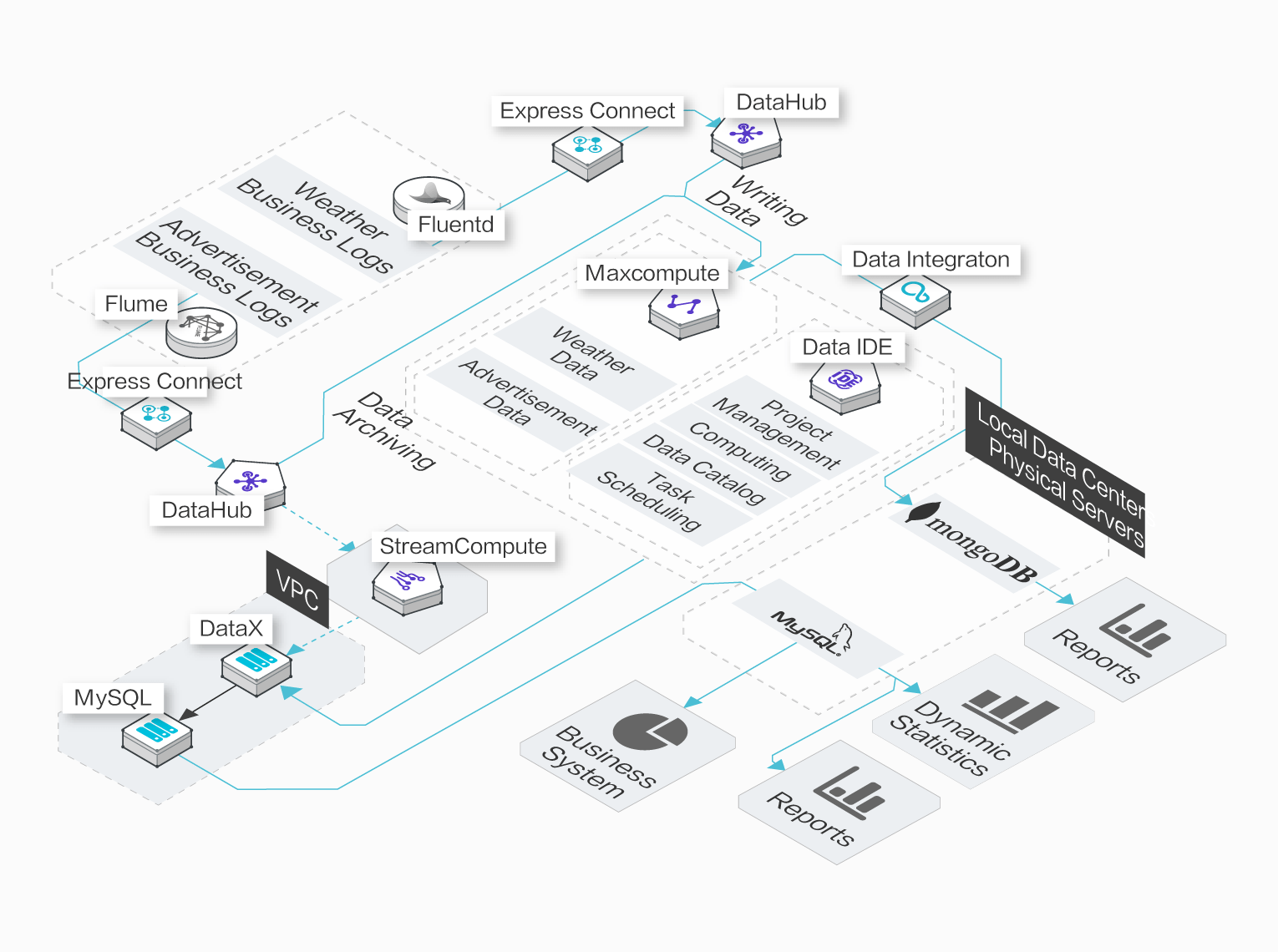
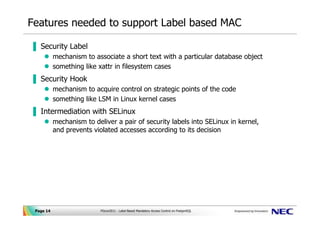
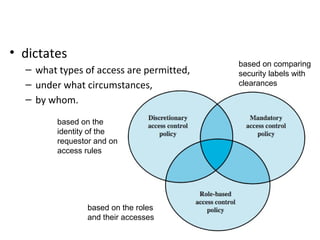























Post a Comment for "41 security labels access control"